Overview
The Lab 3-3 malware that is to be analyized using basic dynamic analysis techniques is:
- Lab03-03.exe
The following are the tasks required to complete the lab exercise:
Basic Dynamic Analysis
Before performing analysis of this malware, my lab environment was setup to have an ubuntu vm with wireshark and inetsim running along with a Windows XP vm running:
- Process Explorer
- Procmon
- ApdateDNS
The two vms were on an internal only network setup so they could see each other on the network but could not communicate with anything else.
Snapshots were taken in this ready state to allow for quick revert / retry if necessary.
Lab Questions
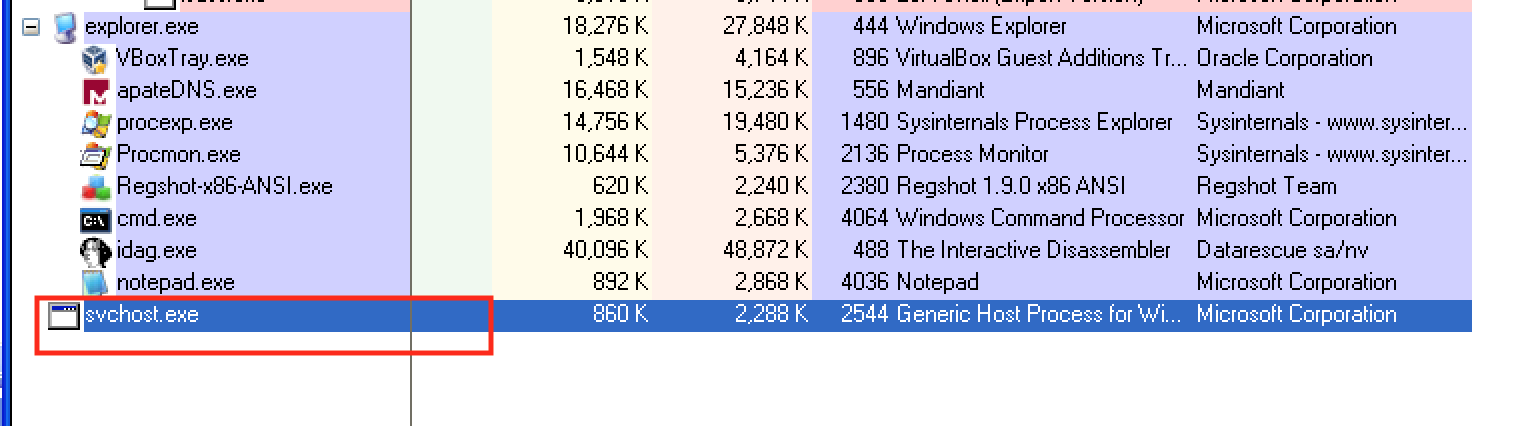
What do you notice when monitoring this malware with Process Explorer?
Viewing Process Explorer while executing the malware shows the malware
executes and exits quickly. I had to run this a couple times to see that
what was actually happening was Lab03-03.exe was spawning a process
called svchost.exe and exiting. This left svchost.exe as an
orphaned process. It is abnormal to have svchost.exe as an orphaned
processes as well as not being a child of service.exe.
Can you identify any live memory modifications?
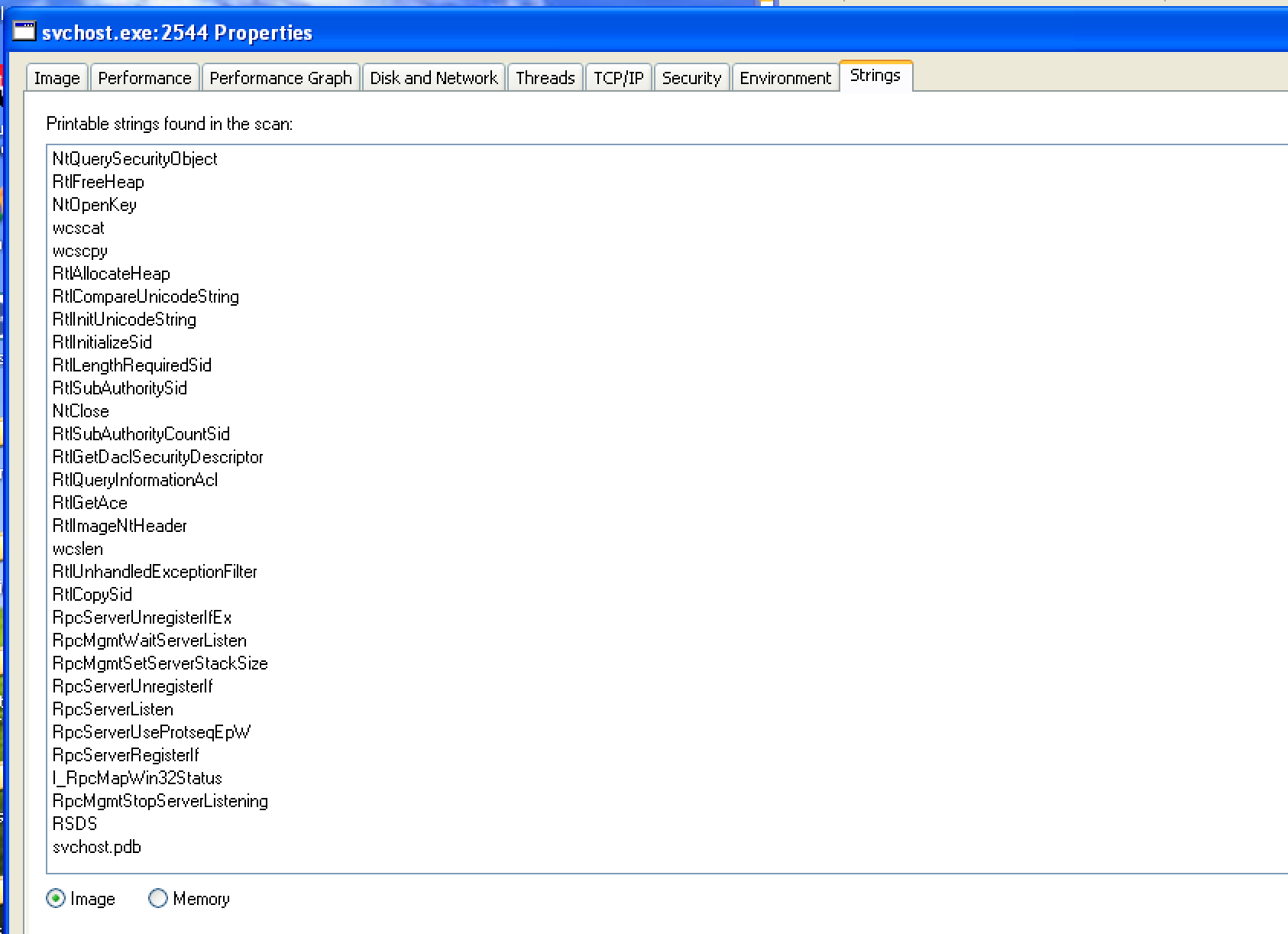
Comparing the strings of svchost.exe in memory and on disk with
Process Explorer reveals some significant differences. The on disk
version contains usual function names. Nothing out of the
ordinary. However, viewing the executable’s strings in memory reveals:
- A log file named
practicalmalwareanalysis.log - Keyboard symbols key names like SHIFT, ENTER, BACKSPACE, CAPS LOCK, etc.
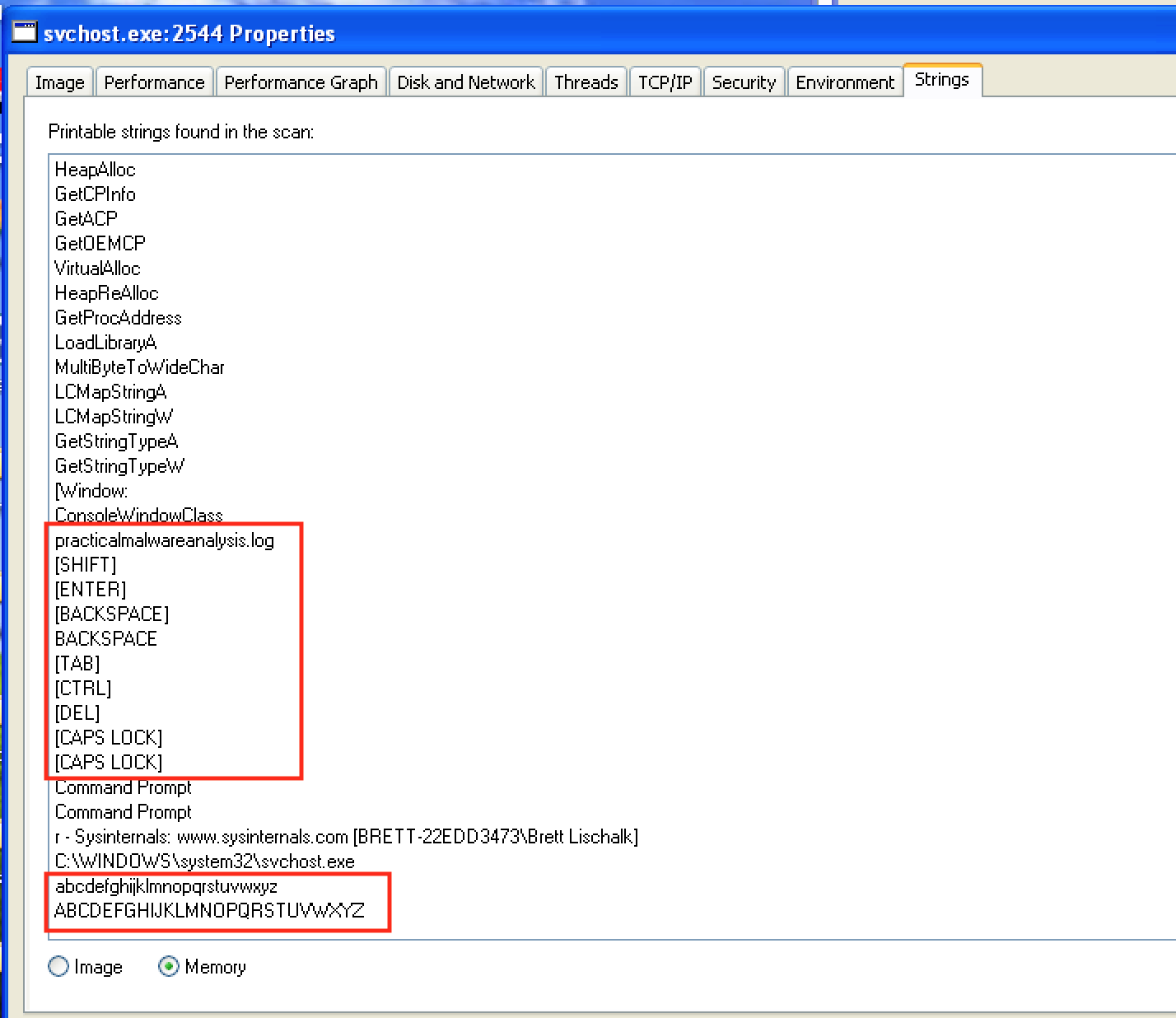
What are the malware’s host-based indicators?
The log file practicalmalwareanalysis.log is created.
What is the purpose of this program?
This program is a keylogger that logs keystrokes to
practicalmalwareanalysis.log.
Conclusion
This was an interesting lab as it highlighted Processes Explorer’s
ability to compare strings in memory vs on disk. It also highlighted
useful things to look for with svchost.exe such as orphaned
svchost.exe processes and svchost.exe processes that are not
children of service.exe.

