This is my analysis of the malware for Lab03-02 from the Practical Malware Analysis book exercises.
Overview
For Lab03-02 we must analyze the malware found in the file
Lab03-02.dll using basic dynamic analysis tools.
The following are the tasks required to complete the lab exercise:
Analysis
Basic Analysis
Before performing any dynamic analysis we want to see what sort of information can be gathered without having to run the malware first.
Strings
Looking at the strings this malware contains reveals:
strings Lab03-02.dll
!This program cannot be run in DOS mode.
.. snip ..
GetProcAddress
LoadLibraryA
RegisterServiceCtrlHandlerA
RegSetValueExA
RegCreateKeyA
CloseServiceHandle
CreateServiceA
OpenSCManagerA
RegCloseKey
RegQueryValueExA
RegOpenKeyExA
DeleteService
OpenServiceA
SetServiceStatus
ADVAPI32.dll
WSASocketA
WS2_32.dll
InternetReadFile
HttpQueryInfoA
HttpSendRequestA
HttpOpenRequestA
InternetConnectA
InternetOpenA
InternetCloseHandle
WININET.dll
Lab03-02.dll
Install
ServiceMain
UninstallService
installA
uninstallA
Y29ubmVjdA==
practicalmalwareanalysis.com
serve.html
Windows XP 6.11
CreateProcessA
kernel32.dll
HTTP/1.1
DependOnService
RpcSs
ServiceDll
Depends INA+, Collects and stores network configuration and location information
, and notifies applications when this information changes.
ImagePath
%SystemRoot%\System32\svchost.exe -k
SYSTEM\CurrentControlSet\Services\
CreateService(%s) error %d
Intranet Network Awareness (INA+)
%SystemRoot%\System32\svchost.exe -k netsvcs
OpenSCManager()
You specify service name not in Svchost//netsvcs, must be one of following:
RegQueryValueEx(Svchost\netsvcs)
netsvcs
RegOpenKeyEx(%s) KEY_QUERY_VALUE success.
RegOpenKeyEx(%s) KEY_QUERY_VALUE error .
SOFTWARE\Microsoft\Windows NT\CurrentVersion\Svchost
IPRIP
uninstall success
OpenService(%s) error 2
OpenService(%s) error 1
uninstall is starting
.?AVtype_info@@
.. snip ..Of particular interest are:
practicalmalwareanalysis.com
RegSetValueExA
RegCreateKeyA
CloseServiceHandle
CreateServiceA
RegCloseKey
RegQueryValueExA
RegOpenKeyExA
DeleteService
OpenServiceA
SetServiceStatus
InternetReadFile
HttpQueryInfoA
HttpSendRequestA
HttpOpenRequestA
InternetConnectA
InternetOpenA
InternetCloseHandle
SOFTWARE\Microsoft\Windows NT\CurrentVersion\Svchost
IPRIPBased on the strings we see, it appears that the malware will most
likely attempt to make an internet connection to
practicalmalwareanalysis.com. It also appears that this malware
modifies the registry and installs a service.
Lab Questions
How can you get this malware to install itself?
Since this malware is a Windows DLL we have a couple of options for how
we can get it to install itself. We can either utilize rundll32.exe
which is provided by Windows or we can attempt to modify the DLL PE
header and change its extension to force Windows to load the DLL as
it would an executable. Let’s try the former.
To utilize rundll32.exe we will need to know the name of the DLL we
wan to analyze and the function name or ordinal of an exported
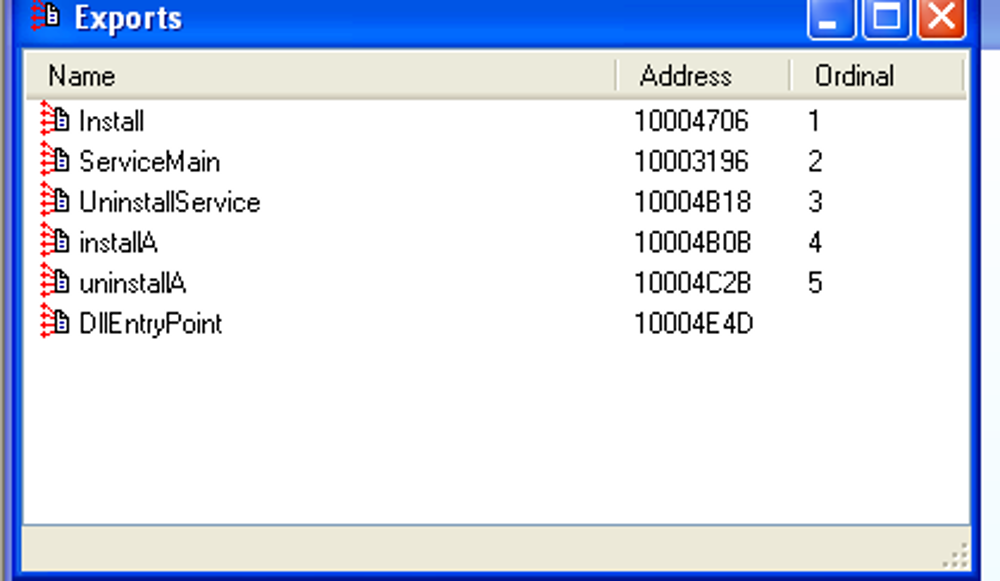
function. Utilizing IDA Pro we can see what functions the DLL
exports. Reviewing the exports we see a function called installA.:
Before attempting to run the DLL, we will want to do a bit of preparation. We will:
- Take a snapshot of the registry with
RegShot - Setup
ApateDNSto look for DNS requests - Setup
Process Explorerto monitor the processes on the system - Take a snapshot of the VirtualBox VM to revert
We proceed to attempt to install the malware with rundll32.exe
Lab03-02.dll installA. After installation another registry snapshot
is taken and a comparison made. The comparison yields:
----------------------------------
Keys added: 9
----------------------------------
HKLM\SYSTEM\ControlSet001\Services\IPRIP
HKLM\SYSTEM\ControlSet001\Services\IPRIP\Parameters
HKLM\SYSTEM\ControlSet001\Services\IPRIP\Security
HKLM\SYSTEM\CurrentControlSet\Services\IPRIP
HKLM\SYSTEM\CurrentControlSet\Services\IPRIP\Parameters
HKLM\SYSTEM\CurrentControlSet\Services\IPRIP\Security
HKU\S-1-5-21-2025429265-1708537768-1060284298-1003\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSaveMRU\hivu
HKU\S-1-5-21-2025429265-1708537768-1060284298-1003\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.hivu
HKU\S-1-5-21-2025429265-1708537768-1060284298-1003\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.hivu\OpenWithList
----------------------------------
Values added: 37
----------------------------------
HKLM\SYSTEM\ControlSet001\Services\IPRIP\Type: 0x00000020
HKLM\SYSTEM\ControlSet001\Services\IPRIP\Start: 0x00000002
HKLM\SYSTEM\ControlSet001\Services\IPRIP\ErrorControl: 0x00000001
HKLM\SYSTEM\ControlSet001\Services\IPRIP\ImagePath: "%SystemRoot%\System32\svchost.exe -k netsvcs"
HKLM\SYSTEM\ControlSet001\Services\IPRIP\DisplayName: "Intranet Network Awareness (INA+)"
HKLM\SYSTEM\ControlSet001\Services\IPRIP\ObjectName: "LocalSystem"
HKLM\SYSTEM\ControlSet001\Services\IPRIP\Description: "Depends INA+, Collects and stores network configuration and location information, and notifies applications when this information changes."
HKLM\SYSTEM\ControlSet001\Services\IPRIP\DependOnService: 52 00 70 00 63 00 53 00 73 00 00 00 00 00
HKLM\SYSTEM\ControlSet001\Services\IPRIP\Parameters\ServiceDll: "C:\Documents and Settings\Brett Lischalk\Desktop\Practical Malware Analysis Labs\BinaryCollection\Chapter_3L\Lab03-02.dll"
HKLM\SYSTEM\ControlSet001\Services\IPRIP\Security\Security: 01 00 14 80 90 00 00 00 9C 00 00 00 14 00 00 00 30 00 00 00 02 00 1C 00 01 00 00 00 02 80 14 00 FF 01 0F 00 01 01 00 00 00 00 00 01 00 00 00 00 02 00 60 00 04 00 00 00 00 00 14 00 FD 01 02 00 01 01 00 00 00 00 00 05 12 00 00 00 00 00 18 00 FF 01 0F 00 01 02 00 00 00 00 00 05 20 00 00 00 20 02 00 00 00 00 14 00 8D 01 02 00 01 01 00 00 00 00 00 05 0B 00 00 00 00 00 18 00 FD 01 02 00 01 02 00 00 00 00 00 05 20 00 00 00 23 02 00 00 01 01 00 00 00 00 00 05 12 00 00 00 01 01 00 00 00 00 00 05 12 00 00 00
HKLM\SYSTEM\CurrentControlSet\Services\IPRIP\Type: 0x00000020
HKLM\SYSTEM\CurrentControlSet\Services\IPRIP\Start: 0x00000002
HKLM\SYSTEM\CurrentControlSet\Services\IPRIP\ErrorControl: 0x00000001
HKLM\SYSTEM\CurrentControlSet\Services\IPRIP\ImagePath: "%SystemRoot%\System32\svchost.exe -k netsvcs"
HKLM\SYSTEM\CurrentControlSet\Services\IPRIP\DisplayName: "Intranet Network Awareness (INA+)"
HKLM\SYSTEM\CurrentControlSet\Services\IPRIP\ObjectName: "LocalSystem"This seems to indicate that the malware has been installed successfully.
How would you get this malware to run after instalation?
We can see that a new service called IPRIP has had registry entries
added for it. Since we know the service name we may now attempt to
start the service and begin dynamic analysis. We can attempt to
start the service using:
net start IPRIPLooking at ApateDNS it indicates that the malware did attempt to
make a connection to practicalmalwareanalysis.com. It appears that
we have successfully run the installed malware.
How can you find the process under which this malware is running?
After starting the service we do a search for Lab03-02.dll in
Process Explorer. We can see in process explorer that Lab03-02.dll
has been loaded into svchost.exe with pid 1048.
Which filters could you set in order to use procmon to glean information?
In procmon the pid can be used as the filter.
What are the malware’s host-based indicators?
The malware installs a service called IPRIP. It has a display name of Intranet Network Awareness (INA+). It’s description is, “Depends INA+, Collects and stores network configuration and location information , and notifies applications when this information changes.”
It writes:
HKLM\SYSTEM\ControlSet001\Services\IPRIP\Parameters\ServiceDll:
%CurrentDirectory%\Lab03-02.dll in the registry for persistence.
Are there any useful network-based signatures for this malware?
It attempts to do a GET request to practicalmalwareanalysis.com/serve.html over port 80 with User-Agent:
%ComputerName% Windows XP 6.11

