This is my analysis of the malware for Lab03-01 from the Practical Malware Analysis book exercises.
Overview
The Lab 3-1 malware that is to be analyized using basic dynamic
analysis techniques consists of the file Lab03-01.exe.
The following are the tasks required to complete the lab exercise:
Analysis
To analyze the malware, basic static analysis will be performed first. Once the information that can be gathered is exhausted, further analysis utilizing basic dynamic analysis techniques will be performed.
Basic Static Analysis
What Are This Malware’s Imports and Strings?
PEView
Using PEView we can look at what imports the executable leverages. In doing so we see that there is not much:
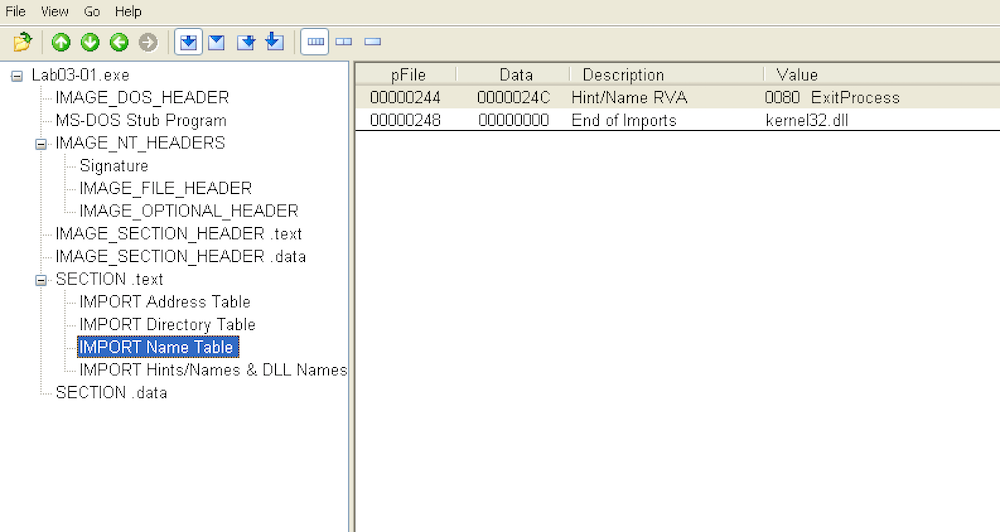
The only import that seems to be used is ExitProcess from kernel32.
IDA Pro
Opening the executable in IDA Pro reveals the same:
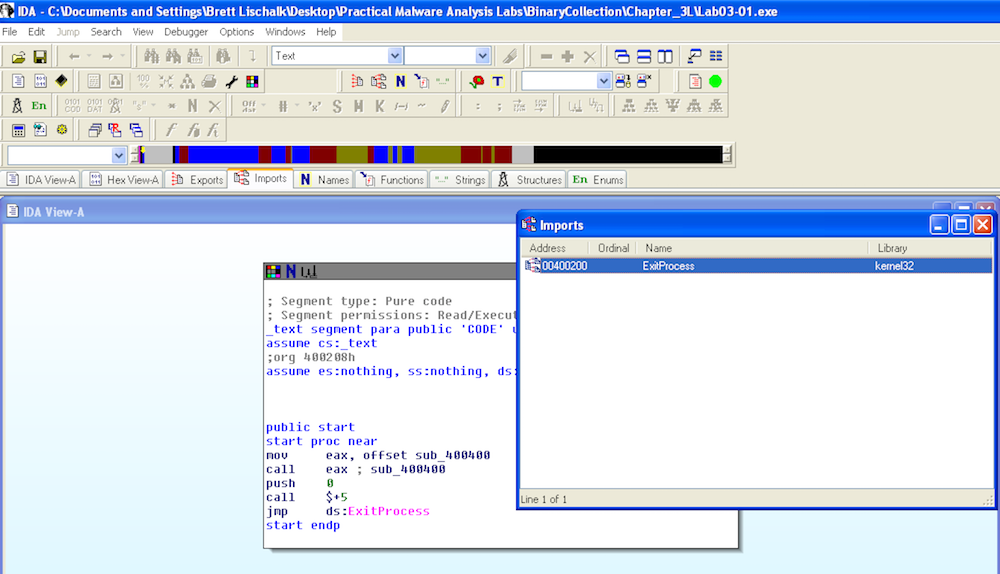
This would seem to indicate that the file is packed. Our next step is to look at the strings.
Strings
Running on strings on the Lab03-01.exe reveals the following:
strings Lab03-01.exe
!This program cannot be run in DOS mode.
Rich
.text
`.data
ExitProcess
kernel32.dll
CONNECT %s:%i HTTP/1.0
advapi32
ntdll
user32
QQVP
advpack
StubPath
SOFTWARE\Classes\http\shell\open\commandV
Software\Microsoft\Active Setup\Installed Components\
test
www.practicalmalwareanalysis.com
admin
VideoDriver
WinVMX32-
vmx32to64.exe
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
AppDataBased on the amount of strings that are revealed it seems to indicate that this executable is actually not packed. A packed executable would normally not reveal so many strings. From the strings that are revealed we find some interesting things:
- www.practicalmalwareanalysis.com
- SOFTWARE\Microsoft\Windows\CurrentVersion\Run
- SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
- WinVMX32
- VideoDriver
- vmx32-to64.exe
Basic Dynamic Analysis
Basic Dynamic Analysis begins with a bit of setup. We:
- Configure and start
ApateDNSon the target machine. The configuration will resolve DNS requests to the ip of another vm setup to pretend to be the actual server the malware would want to connect to. - Start
Process Exploreron the target machine to look at dll’s and mutexes. - Start and clear
Process Monitorto monitor what the malware does while executing. - Start
netcatlistening on the honeypot vm that will be pretending to be a real service the malware is trying to connect to.
With this setup in place the malware is executed and the following results are derived…
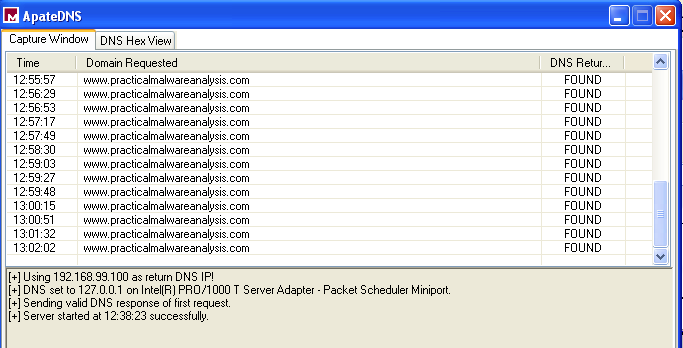
ApateDNS
Within ApateDNS it is aparant that an attempt is made by the malware
to reachout to www.practicalmalware.com. This is consistent with
what was expected based on what was seen while analyzing the strings
that are utilized by the malware.
Process Explorer
Within Process Explorer we look for a couple things. We first notice
that the malware creates a mutex called WinVMX32:
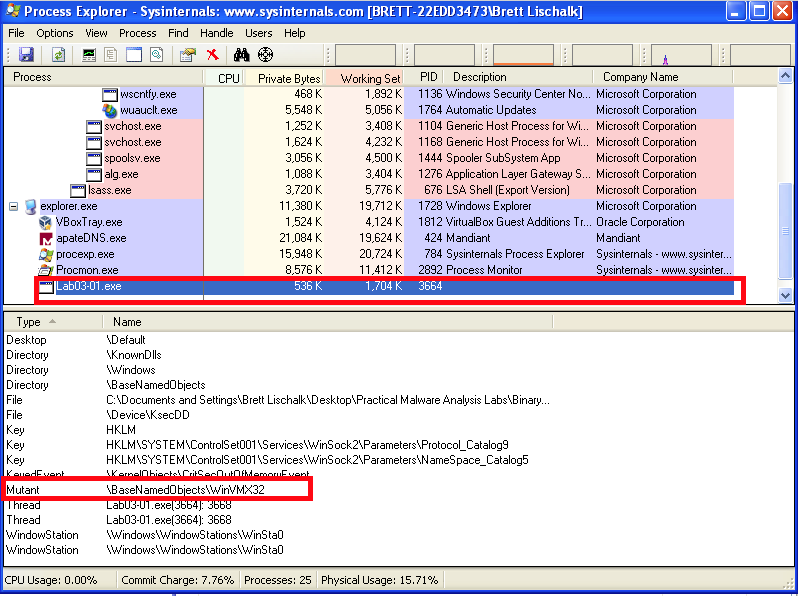
Malware often creates mutexes to prevent multiple instances of the malware from attempting to infect the same macine. If an instance of the malware is unable to obtain a handle to the named mutex, then the malware will exit. The existence of a particular named mutex can be used as a host based indicator that a host is infected.
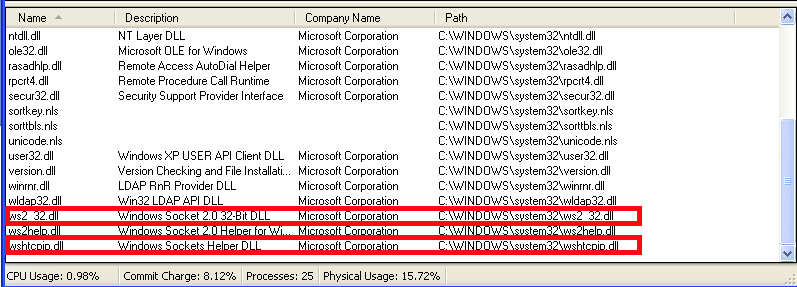
The next thing that can be analyzed is the dll's. Looking at the
listing of dll’s that the malware includes at runtime, we can see:
ws2_32.dllwshtcp_ip.dll
ws2_32.cll is the socket library used for dealing with network
connections. wshtcp_ip.dll, according to the properties, indicates
that it is a “Windows Sockets Helper DLL”. The presence of socket
dll’s indicates network activity which we already verified by the DNS
request that the malware made.
Process Monitor
Filtering Process Monitor to focus in on the Lab03-01.exe process
and the operations RegSetValue and WriteFile, it can be seen that
the malware modifies a registry entry and creates a file on the
filesystem.
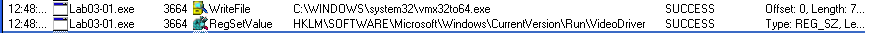
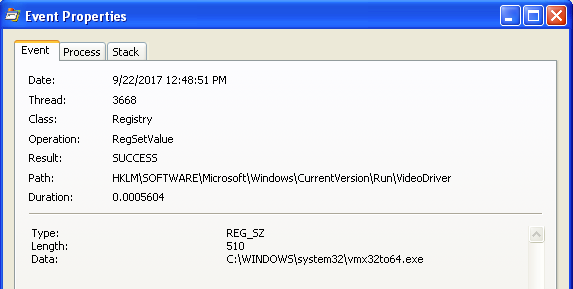
Looking at the properties of the registry modification in Processes
Explorer we can see that an executable vmx32to64.exe is set to run
on startup. This is the file that is written to the filesystem by the
malware.
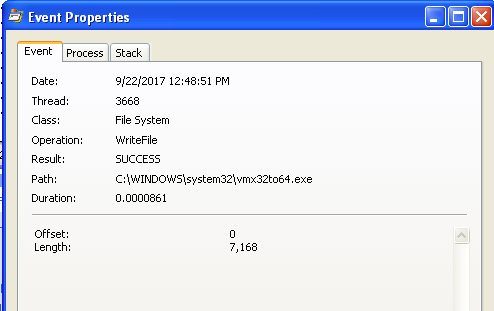
Looking at the properties of the WriteFile operation we can see that
7,168 bytes were written to the file system. This is the same size as
Lab03-01.exe.
If we look at the checksum’s of both files we can see that they are in fact the same file:
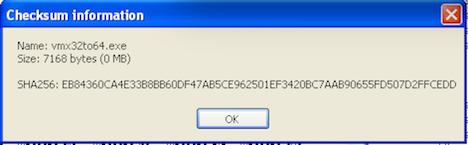
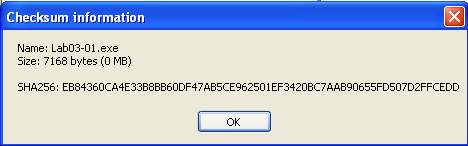
Netcat and Wireshark
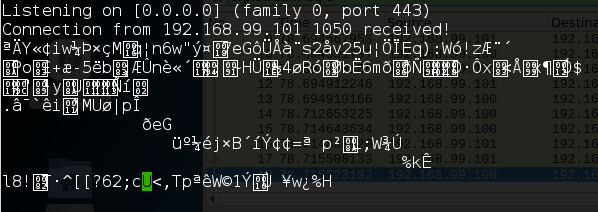
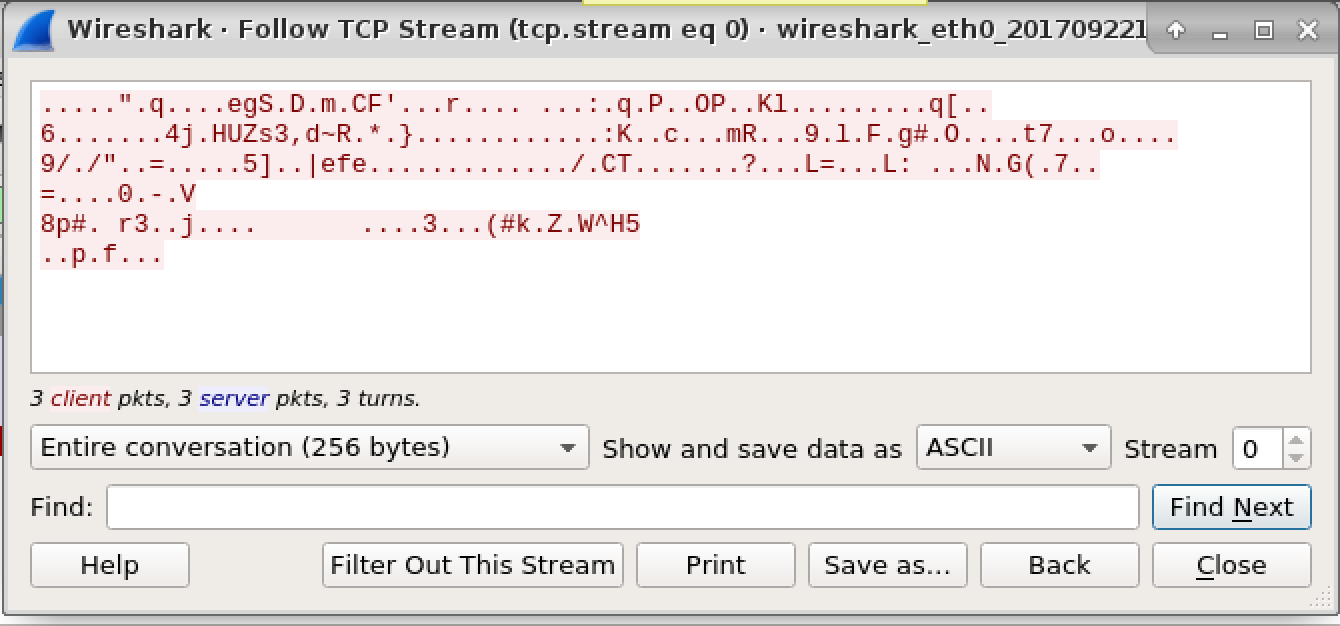
Observing what netcat and wireshark receive when the malware runs
reveals that a random 256 bytes appear to be sent as a
“beacon”. Malware often utilizes a beacon to let a “command and control”
server know that the malware is ready to roll.
The Questions
What Are This Malware’s Imports and Strings?
The only import that is found is ExitProcess. A bunch of interesting
strings are found:
- www.practicalmalwareanalysis.com
- SOFTWARE\Microsoft\Windows\CurrentVersion\Run
- WinVMX32
- VideoDriver
- vmx32-to64.exe
Through our basic dynamic analysis we learn that these are all used by
the malware during execution. www.practicalmalwareanalysis.com is
where the malware phone’s home
to. SOFTWARE\Microsoft\Windows\CurrentVersion\Run is the registry
entry that is used to start the malware on system start. WinVMX32 is
the name of the mutex that is created to prevent multiple instances of
the malware from infecting the same computer. VideoDriver is the
registry entry key that is used. vmx32-to64.exe is the malware that
gets written and started at system startup.
What Are The Malware’s Host-Based Indicators?
Host based indicators include:
- A mutex called
WinVMX32 - The presence of
vmx32-to64.exeinC:\WINDOWS\system32 - A registry entry of
VideoDriver
Are There Any Useful Network-Based Signatures for This Malware? If So, What Are They?
I am not sure that there are network-based “signatures” of the malware
as the requests include random bytes. A network based indicator that
the malware is present would be requests being made to
www.practicalmalwareanalysis.com.

