This is my analysis of the malware for Lab01-04 from the Practical Malware Analysis book exercises.
Overview
The Lab 1-4 malware that is to be analyized using basic static
analysis techniques consists of the file Lab01-04.exe.
The following are the tasks required to complete the lab exercise:
Basic Static Analysis
VirusTotal?
Upload the Lab01-04.exe file to http://www.virustotal.com. Does it match any existing antivirus definitions?
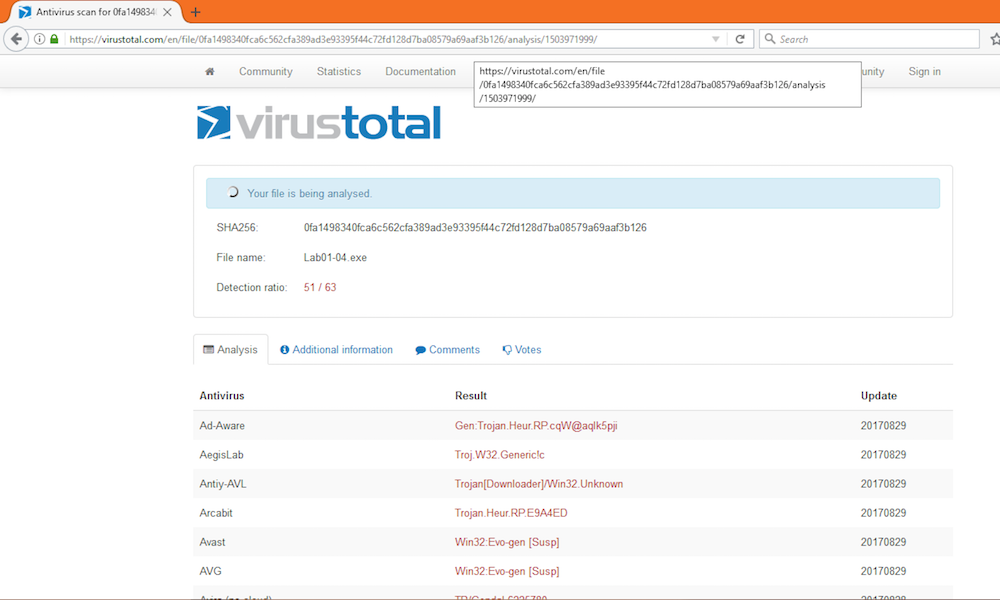
According to VirusTotal, this malware does match existing antivirus definitions.
Packed or Obfuscated?
Are there any indications that this file is packed or obfuscated? If so, what are these indicators? If the file is packed, unpack it if possible.
Strings
Running strings on the executable yields:
PS C:\Users\Brett\Desktop\Practical Malware Analysis Labs\BinaryCollection\Chapter_1L> strings .\Lab01-04.exe
Strings v2.53 - Search for ANSI and Unicode strings in binary images.
Copyright (C) 1999-2016 Mark Russinovich
Sysinternals - www.sysinternals.com
!This program cannot be run in DOS mode.
.. snip ..
Rich
.text
`.rdata
@.data
.rsrc
CloseHandle
OpenProcess
GetCurrentProcess
CreateRemoteThread
GetProcAddress
LoadLibraryA
WinExec
WriteFile
CreateFileA
SizeofResource
LoadResource
FindResourceA
GetModuleHandleA
GetWindowsDirectoryA
MoveFileA
GetTempPathA
KERNEL32.dll
AdjustTokenPrivileges
LookupPrivilegeValueA
OpenProcessToken
ADVAPI32.dll
_snprintf
MSVCRT.dll
_exit
_XcptFilter
exit
__p___initenv
__getmainargs
_initterm
__setusermatherr
_adjust_fdiv
__p__commode
__p__fmode
__set_app_type
_except_handler3
_controlfp
_stricmp
winlogon.exe
<not real>
SeDebugPrivilege
sfc_os.dll
\system32\wupdmgr.exe
%s%s
BIN
#101
EnumProcessModules
psapi.dll
GetModuleBaseNameA
psapi.dll
EnumProcesses
psapi.dll
\system32\wupdmgr.exe
%s%s
\winup.exe
%s%s
BIN
!This program cannot be run in DOS mode.
Rich
.text
`.rdata
@.data
.. snip ..
GetWindowsDirectoryA
WinExec
GetTempPathA
KERNEL32.dll
URLDownloadToFileA
urlmon.dll
_snprintf
MSVCRT.dll
_exit
_XcptFilter
exit
__p___initenv
__getmainargs
_initterm
__setusermatherr
_adjust_fdiv
__p__commode
__p__fmode
__set_app_type
_except_handler3
_controlfp
\winup.exe
%s%s
\system32\wupdmgrd.exe
%s%s
http://www.practicalmalwareanalysis.com/updater.exeWe can see that there is actually quite a bit of information found by using the strings application. It is probably safe to say that this is not packed or obfuscated. Let’s check out IDApro just to be safe.
IDAPro
IDAPro has no issues loading the file so no alerts of packing or obfuscation are given. The instructions that are outlined seem to be very clear as it can bee seen which libraries are getting loaded and which functions are getting called.
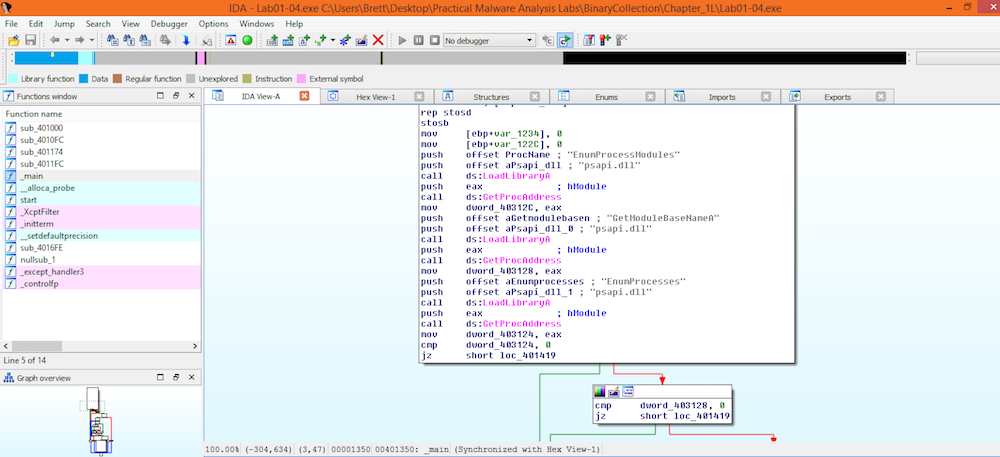
At this point I’m convinced that this is not packed or obfuscated.
Imports Hint at Functionality?
The imports indicate a few things:
LoadResource, FindResource, and SizeOfResourceindicate that data is loaded from the resource sectionGetWindowsDirectoryindicates that files may be written to the system directoryWinExecindicates that a program gets executedCreateFileandWriteFileindicate that a file gets created and written toURLDownloadToFileApoints at something being downloaded to a fileEnumProcessesgets an array of process idsSeDebugPrivilegeindicates that this malware may inject code into another process it doesn’t own
Host- or Network-Based Indicators?
For host based indicators the following files could indicate that the host is infected:
\winup.exe\system32\wupdmgrd.exe\system32\wupdmgr.exe
Network activity to
http://www.practicalmalwareanalysis.com/updater.exe could be a
network based indicator that this malware is present.
Bonus Round: Resource Section
Because the imports seem to indicate that something is loaded from the resource section, Resource Hacker can be used to see what may live there:
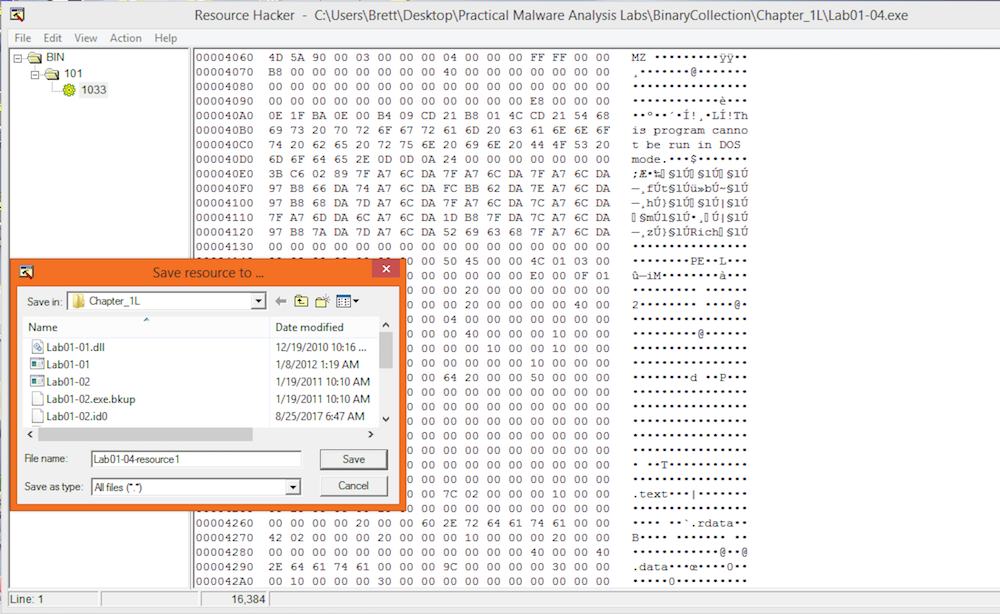
The string we found earlier “!This program cannot be run in DOS mode.” appears to indicate that this binary is actually another executable living in the resource section. Saving this as a binary lets analyze it just like any other executable.
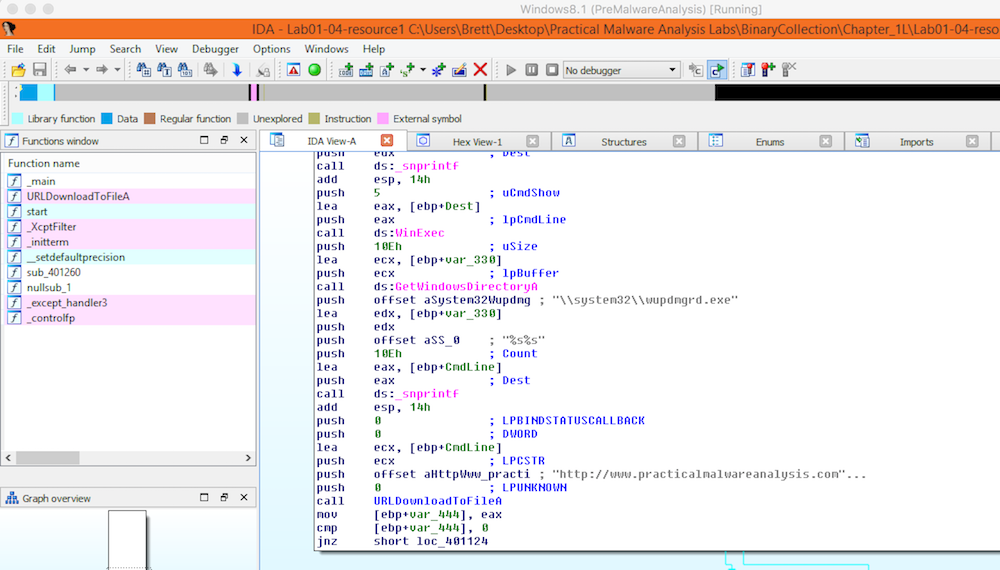
Viewing the executable in IDAPro we can see the instructions that it
tries to perform. In this particular screenshot, we can see it
attempting to call out to
http://www.practicalmalwareanalysis.com/updater.exe.
Conclusion
This malware was particularly interesting because of its use of the resource section to contain another executable. I’m not 100% sure what the advantage of doing something like this might be but upon thinking about it a bit more, I think that by organizing the malware in this way, the particularly malicious parts of the malware don’t appear on the system right away. They show up after the downloader portion is extracted from the resource section of the executable and downloads the main payload, adding 2 layers of obfuscation as to what the malware’s true intentions might be. I wonder what sort of tricks the next lab will hold…

