This is my analysis of the malware for Lab01-03 from the Practical Malware Analysis book exercises.
Overview
The Lab 1-3 malware that is to be analyized using basic static
analysis techniques consists of the file Lab01-03.exe.
The following are the tasks required to complete the lab exercise:
Basic Static Analysis
VirusTotal?
Upload the Lab01-03.exe file to http://www.virustotal.com. Does it match any existing antivirus definitions?
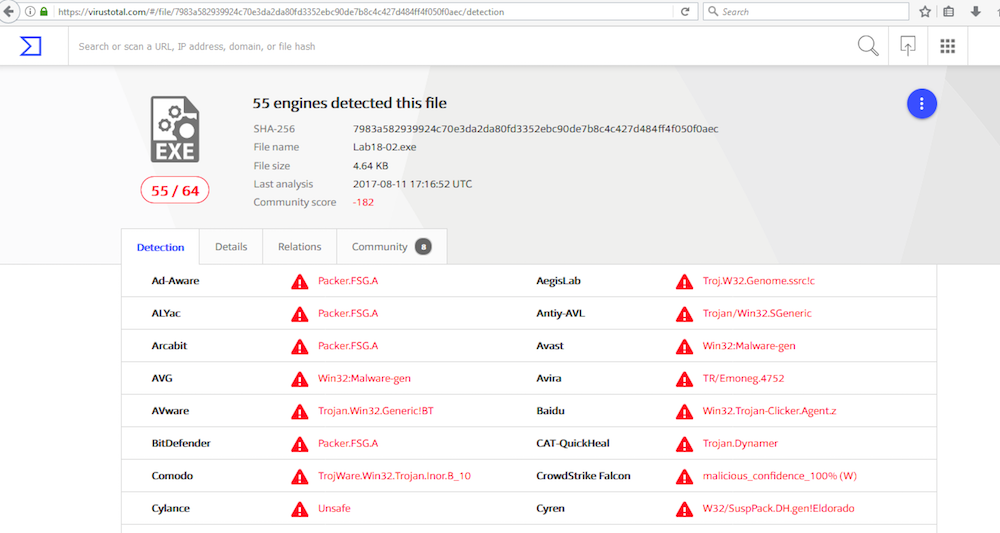
According to VirusTotal this malware has been seen before.
Packed or Obfuscated?
Are there any indications that this file is packed or obfuscated? If so, what are these indicators? If the file is packed, unpack it if possible.
Strings
We can start with strings to see how many legible strings can be
found in the executable:
PS C:\Users\Brett\Desktop\Practical Malware Analysis Labs\BinaryCollection\Chapter_1L> strings Lab01-03.exe
Strings v2.53 - Search for ANSI and Unicode strings in binary images.
Copyright (C) 1999-2016 Mark Russinovich
Sysinternals - www.sysinternals.com
!Windows Program
$PE
b!@
`.rdata
@.data
$s!
;Ot
(Q@
KERNEL32.dll
LoadLibraryA
GetProcAddress
3Bt>O
VQ(8
2]<,M
.. snip ..Running strings seems to only reveal a few strings including
LoadLibraryA and GetProcAddress. Since these functions are often
called in packed malware and there are few other legible strings, it
is looking like this malware may be packed.
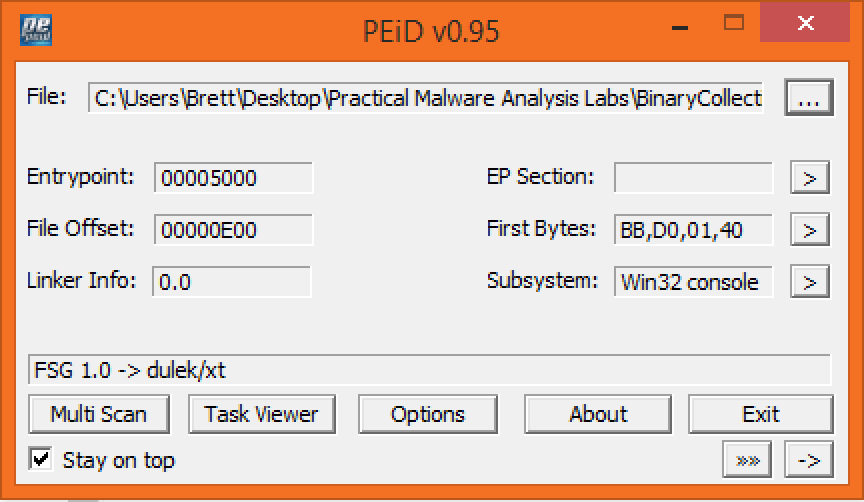
PEid
When we run the executable through PEid we find that PEid has detected
the executable to be packed with fsg 1.0 dulek/xt.
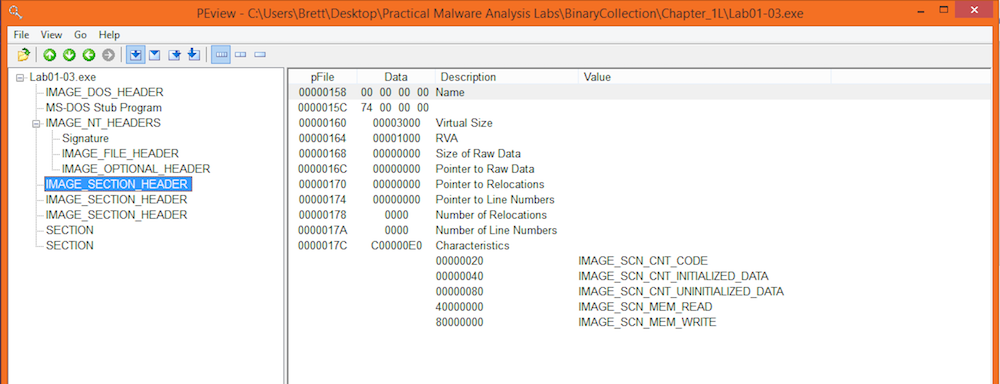
PEView
Running the executable through PEView also leads us to suspect packing as the normal “.text”, “.rdata”, etc. sections are not present. Instead the sections are just called “SECTION”. “Virtual Size” and “Raw Data Size” of the sections are also different in significant amounts seeming to indicate that the executable will expand the malware at runtime.
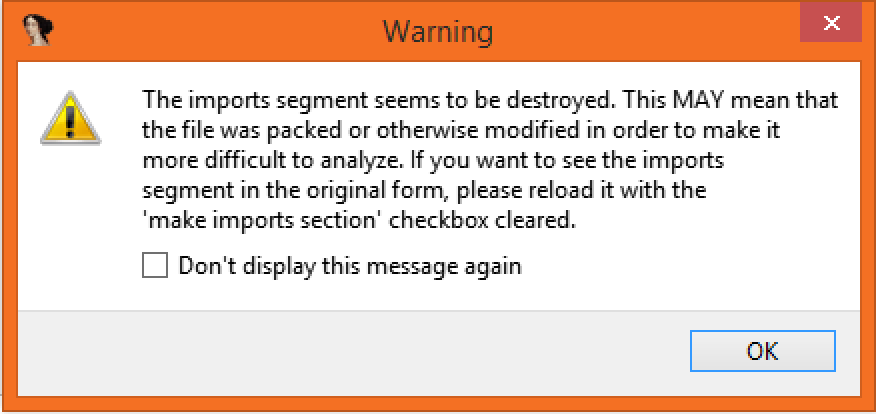
IDAPro
Opening the executable in IDAPro warns that this executable seems to be packed or obfuscated:
Upacking
Practical Malware Analysis has not taught how to deal with unpacking
fsg 1.0 dulek/xt at this point. A little googling seems to indicate
that some manual processes will be necessary. The process is not as
straightforward as just running an un-pack command like with upx. I
may attempt some of these manual processes at some point in the future
but I am going to leave that alone for now as the book has not covered
it.
Imports Hint at Functionality?
Because the only imports that are able to be viewed are LoadLibraryA
and GetProcAddress, a good idea of the functionality can not be
gleaned at this point.
Host- or Network-Based Indicators?
Because no legible strings can be found that would point toward host or network based indicators it is not possible to find any good indicators of this malware at this point.
Conclusion
This concludes the analysis of the third malware of Lab 1 from the Practical Malware Analysis book. A curve ball was thrown with this malware utilizing a packer that is not covered in the book. After looking at the appendix answers for this exercise, everything that could be learned about this malware without knowledge of unpacking fsg 1.0 has been learned. The appendix says that the techniques for further dealing with this malware will be covered in chapter 18. I’ll update this article if I take a stab at researching and trying to unpack it myself before getting to chapter 18.

