This is my analysis of the malware for Lab01-02 from the Practical Malware Analysis book exercises.
Overview
The Lab 1-2 malware that is to be analyized using basic static
analysis techniques consists of the file Lab01-02.exe.
The following are the tasks required to complete the lab exercise:
Basic Static Analysis
VirusTotal?
Upload the Lab01-02.exe file to http://www.virustotal.com. Does it match any existing antivirus definitions?
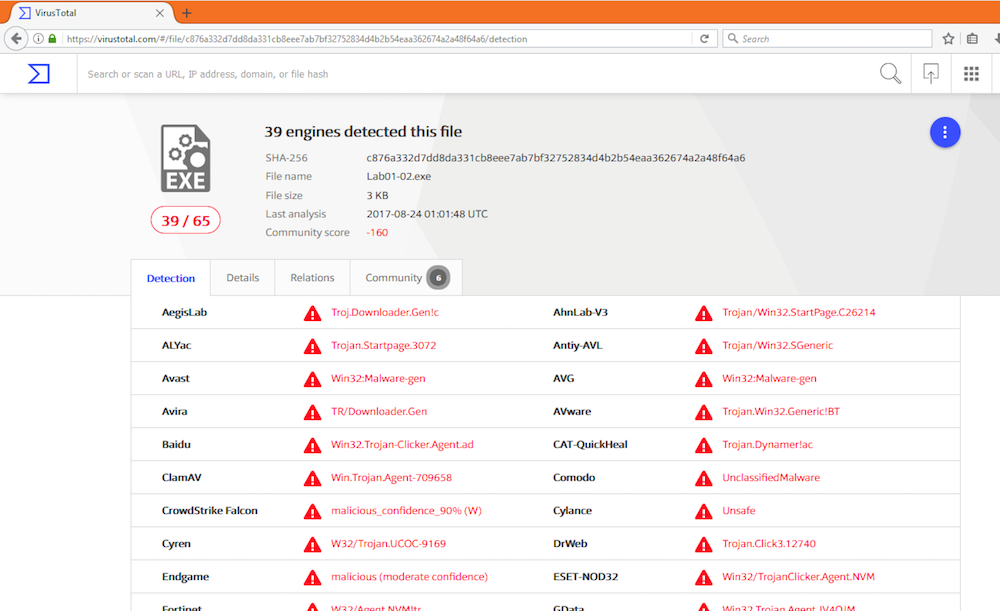
According to VirusTotal this malware has been seen before.
Packed or Obfuscated?
Are there any indications that this file is packed or obfuscated? If so, what are these indicators? If the file is packed, unpack it if possible.
We can gain some insight as to if the malware is packed or obfuscated
in any way using strings, PEid, PEView, and IDAPro.
Strings
Using the strings utility on Lab01-02.exe we see the following:
.. snip ..
KERNEL32.DLL
ADVAPI32.dll
MSVCRT.dll
WININET.dll
LoadLibraryA
GetProcAddress
VirtualProtect
VirtualAlloc
VirtualFree
ExitProcess
CreateServiceA
exit
InternetOpenAThe strings that are found do seem to indicate that the malware might
create a service and reach out to the internet but the list of imports
also seems small. From what was learned in the Practical Malware
Analysis book, a malware that has few strings and has LoadLibary and
GetProcAddress points to a high likelyhood that the malware is
packed. We can gain more insight using PEid.
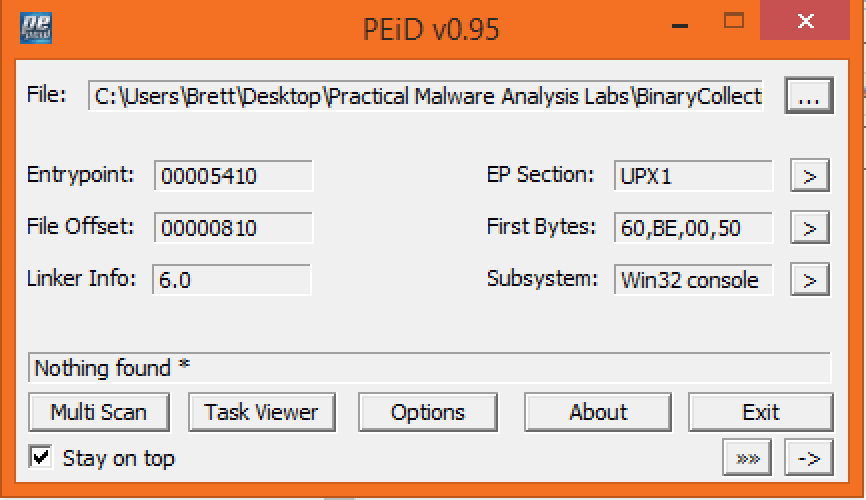
PEid
When running PEid it doesn’t find the usage of a specific packer but the “EP Section” shows UPX1 which seems to point at the usage of a packer.
We can get more information using PEView.
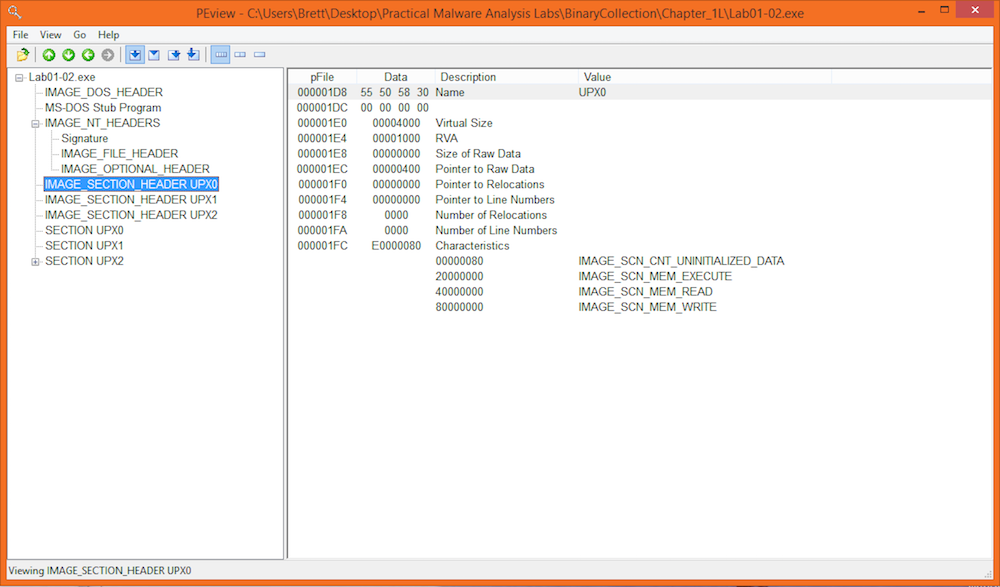
PEView
Looking at the executable in PEView reveals some interesting things that hint at packer use. The sections are called: UPX0, UPX1, and UPX2. Sections of an exeuctable would normally include sections neamed like: “.text”, “.rdata”, and “.data”. The headers of the sections show that the “Virtual Size” is different than the “Raw Data” size. This means that the section takes more space in memory than on disk. This is another indication of packer usage.
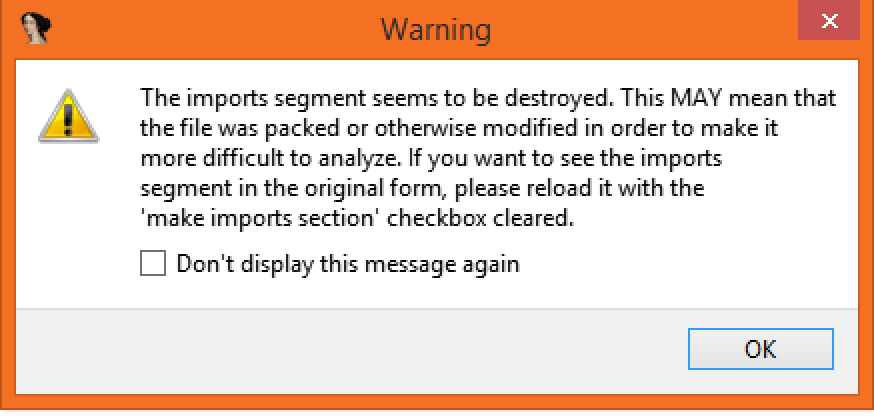
IDAPro
Finally, simply opening the executable in IDAPro warns that this executable seems to be packed or obfuscated:
Proceeding to open the executable anyways shows that the imports list of imports is quite small just like we saw in the usage of Strings.
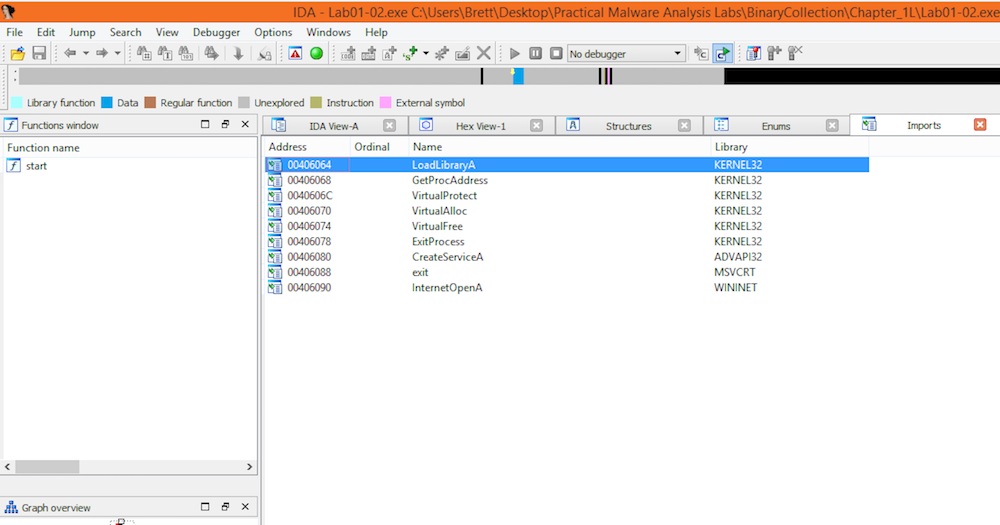
Upacking
At this point it if fairly safe to assume that this executable is packed using the UPX packer. We can unpack the executable using:
PS C:\Users\Brett\Desktop\Practical Malware Analysis Labs\BinaryCollection\Chapter_1L> upx -d Lab01-02.exe
Ultimate Packer for eXecutables
Copyright (C) 1996 - 2013
UPX 3.91w Markus Oberhumer, Laszlo Molnar & John Reiser Sep 30th 2013
File size Ratio Format Name
-------------------- ------ ----------- -----------
16384 <- 3072 18.75% win32/pe Lab01-02.exe
Unpacked 1 file.Now that the executable is unpacked, opening it in IDAPro gives us a different story:
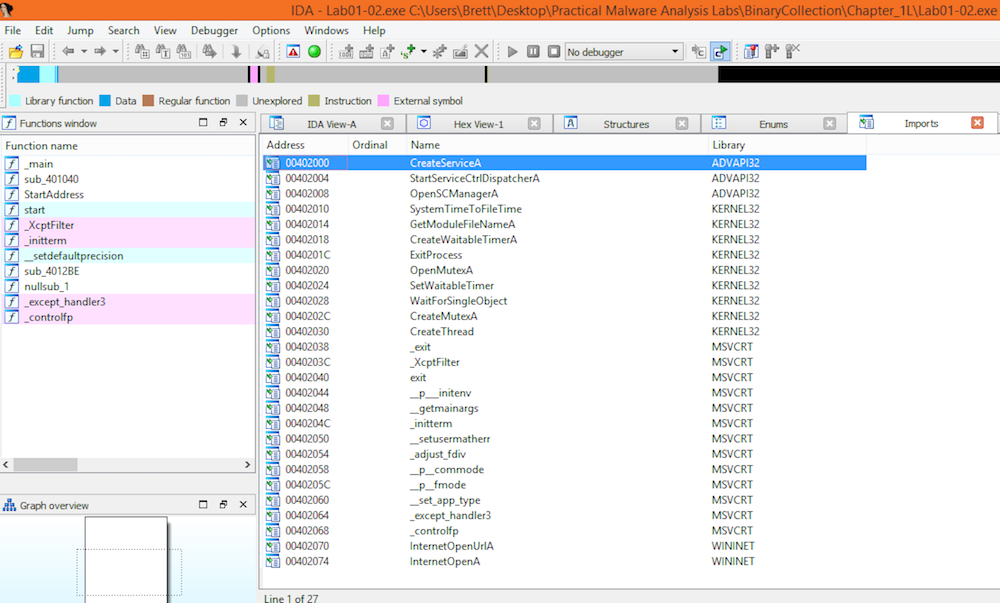
The list of imports has expanded to include many more functions.
Imports Hint at Functionality?
Do any imports hint at this program’s functionality? If so, which imports are they and what do they tell you?
Some of the interesting imports that can be found are:
- CreateServiceA
- StartServiceCtrlDispatcherA
- OpenSCManager
- InternetOpenUrlA
- InternetOpenUrl
Based on these imports it seems that this malware sets up a Windows service. The malware also appears to reach out to a url.
Host- or Network-Based Indicators?
What host- or network-based indicators could be used to identify this malware on infected machines?
Looking at the strings output after the unpacking of the executable
the following strings can be found:
InternetOpenUrlA
InternetOpenA
MalService
Malservice
HGL345
http://www.malwareanalysisbook.com
Internet Explorer 8.0“MalService” seems likely to be the name of the service that would be running on the host. If “MalService” was found in the service list this would be a host-based indicator that the host was infected with the malware.
If network activity was detected going to “http://www.malwareanalysisbook.com”, this would be a strong network-based indicator that the malware was present on the system.
Conclusion
This concludes the analysis of the second malware of Lab 1 from the Practical Malware Analysis book. The techniques utilized where very similar to the techniques needed for the first malware sample with the twist of dealing with a packed malware sample. It will be interesting to see what new twist the next malware may have.

