I am beginning an new series of blog posts to document my research as I work through the Practical Malware Analysis book and labs. This is the first blog post in that series beginning with Lab 1-1.
Overview
The Lab 1-1 malware that is to be analyized using basic static analysis techniques consists of two files:
- Lab01-01.exe
- Lab01-01.dll
The following are the tasks required to complete the lab exercise:
Basic Static Analysis
VirusTotal?
Upload the files to http://www.virustotal.com. Does either file match any existing antivirus signatures?
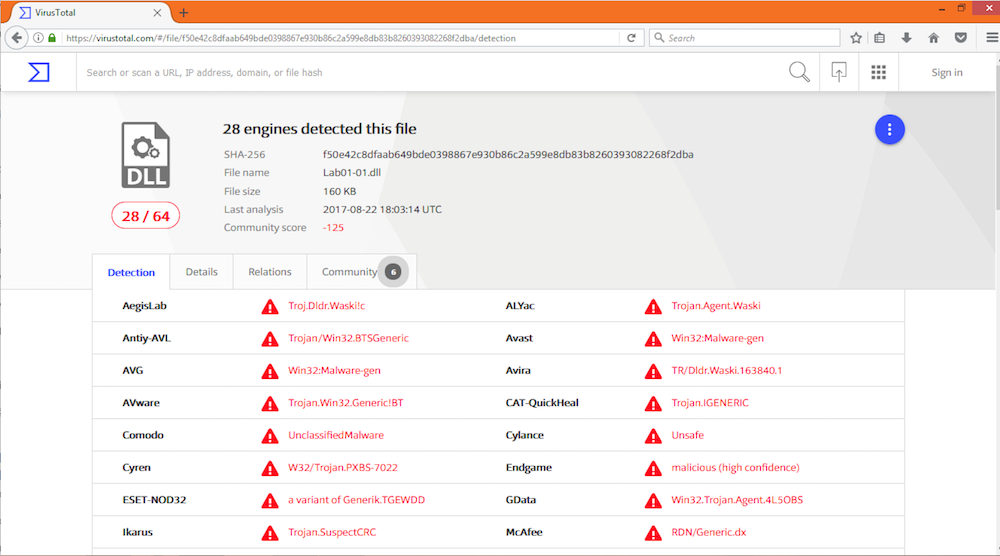
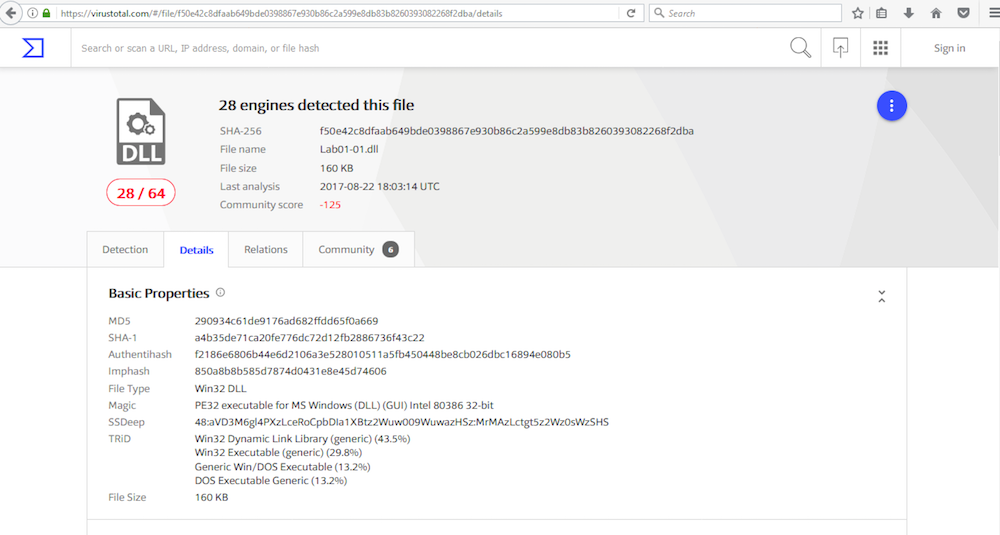
Uploading both files to VirusTotal indicates that both the .exe and .dll match existing signatures. This is depicted in the following screen captures:
Lab01-01.exe
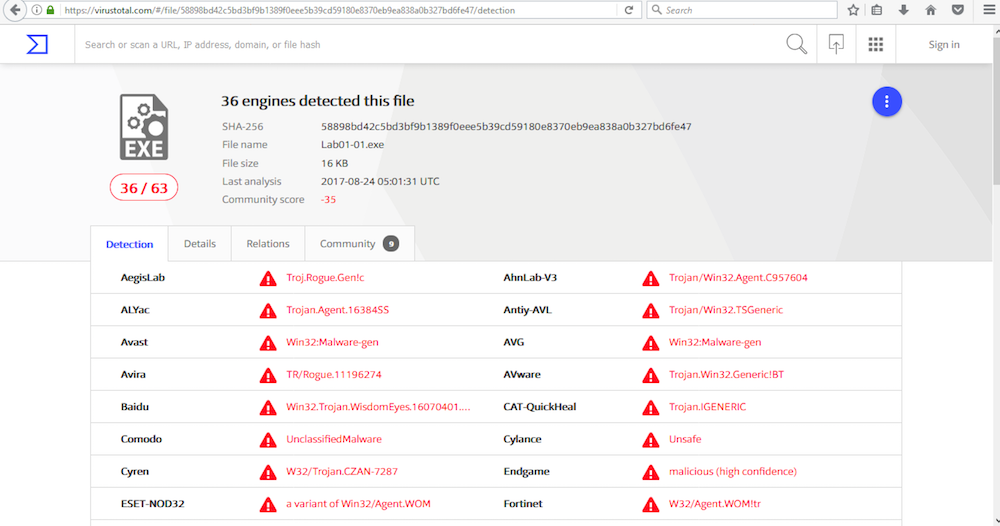
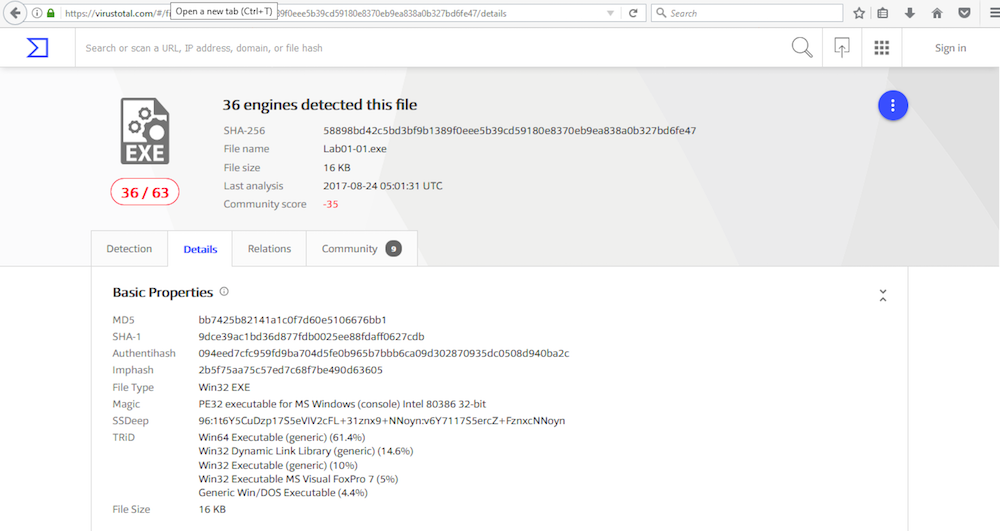
Lab01-01.dll
Compilation Time?
When where these files compiled?
Opening both the dll and exe in PEview should give an idea of when the files were compiled.
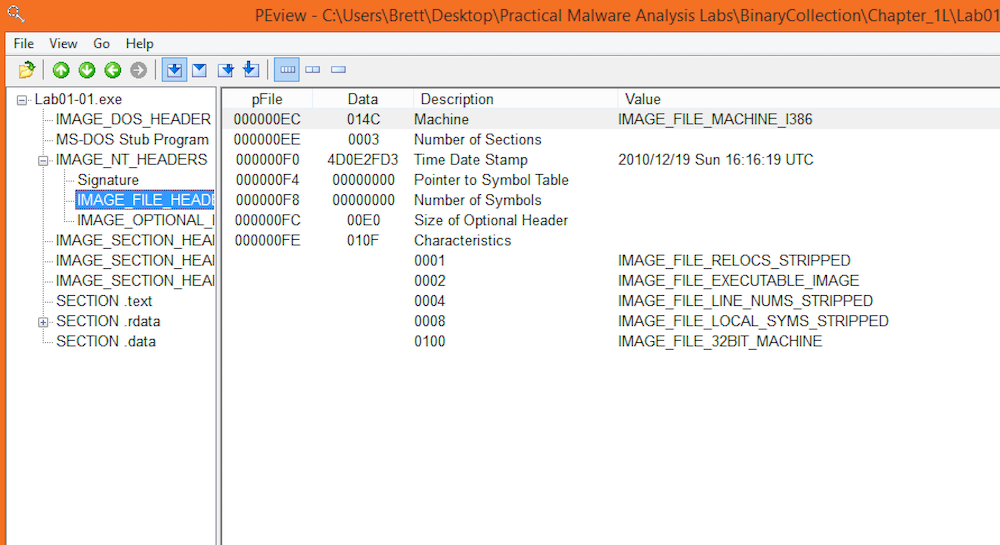
Lab01-01.exe
The executable appears to have been compiled on December 19th, 2010 at 16:16:19 UTC (2010/12/19 Sun 16:16:19 UTC)
Lab01-01.dll
The dll appears to have been compiled on December 19th, 2010 at 16:16:38 UTC (2010/12/19 Sun 16:16:38 UTC)
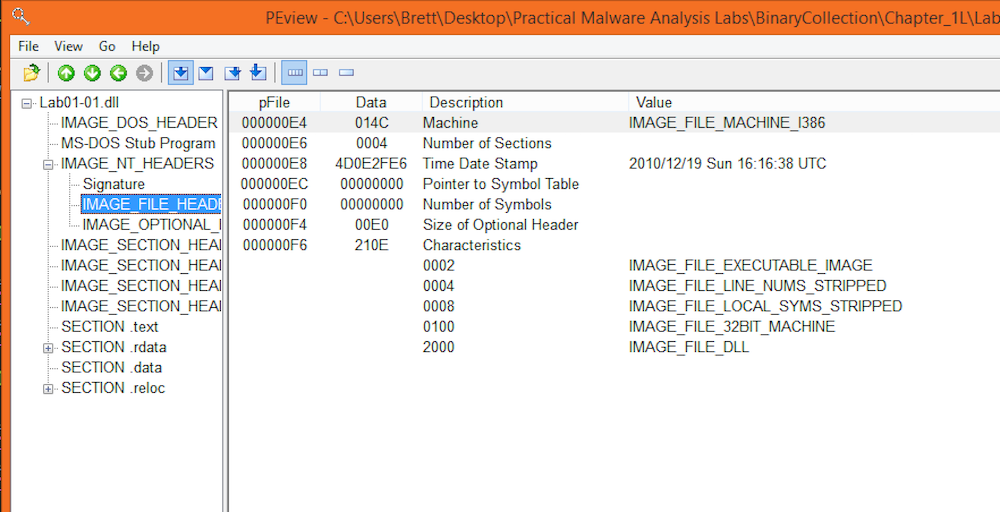
Both the executable and dll compilation times are within a few seconds from one another which seems to indicate that they were compiled in the same compilation process.
Packed or Obfuscated?
Are there any indications that either of these files is packed or obfuscated? If so, what are these indicators?
PEid
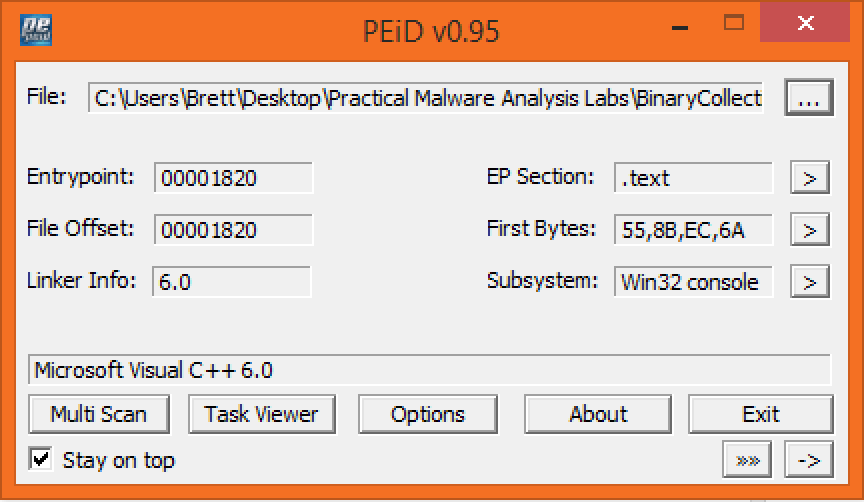
Opening both the executable and dll in PEid is a good first start to check for packer usage:
Lab01-01.exe
Lab01-01.dll
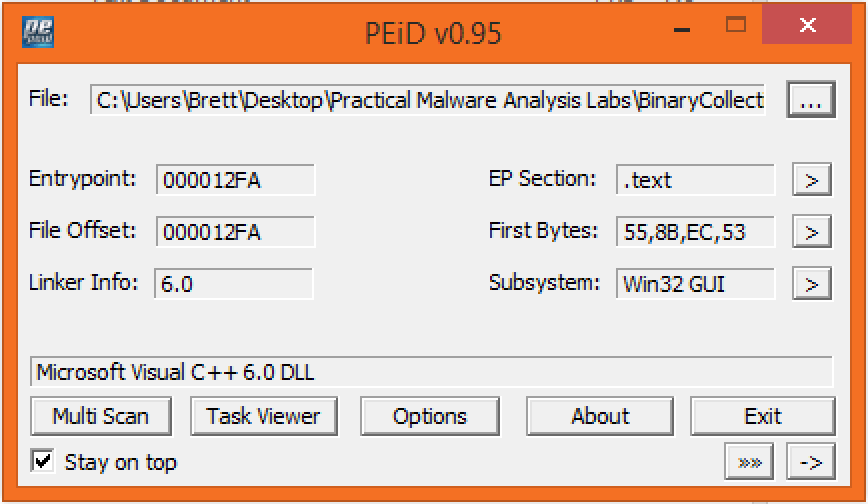
Running the executable and dll through PEid doesn’t show any signs of a packer being used. PEid is able to determine that Microsoft Visual C++ 6.0 appears to be the compiler that was used. The analysis of the dll indicates that the subsystem is Win32 GUI so this seems to indicate that there is a GUI component to this malware.
Another check that can be done to determine if packing or obfuscation
is taking place is the use of the strings utility:
Strings
Running strings on the executable shows:
.. snip ..
CloseHandle
UnmapViewOfFile
IsBadReadPtr
MapViewOfFile
CreateFileMappingA
CreateFileA
FindClose
FindNextFileA
FindFirstFileA
CopyFileA
KERNEL32.dll
malloc
exit
MSVCRT.dll
kerne132.dll
kernel32.dll
.exe
C:\*
C:\windows\system32\kerne132.dll
Kernel32.
Lab01-01.dll
C:\Windows\System32\Kernel32.dll
WARNING_THIS_WILL_DESTROY_YOUR_MACHINEThere seems to be a decent amount of information returned. In the scenario of a packed or obfuscated file, very few legible strings would be found.
Doing the same on the dll shows:
.. snip ..
CloseHandle
Sleep
CreateProcessA
CreateMutexA
OpenMutexA
KERNEL32.dll
WS2_32.dll
strncmp
MSVCRT.dll
free
malloc
exec
sleep
hello
127.26.152.13
SADFHUHF
.. snip ..While not as many strings are returned, there are still seems to be a good amount of information returned. An ip address, exec, sleep, and other functions are found.
IDAPro
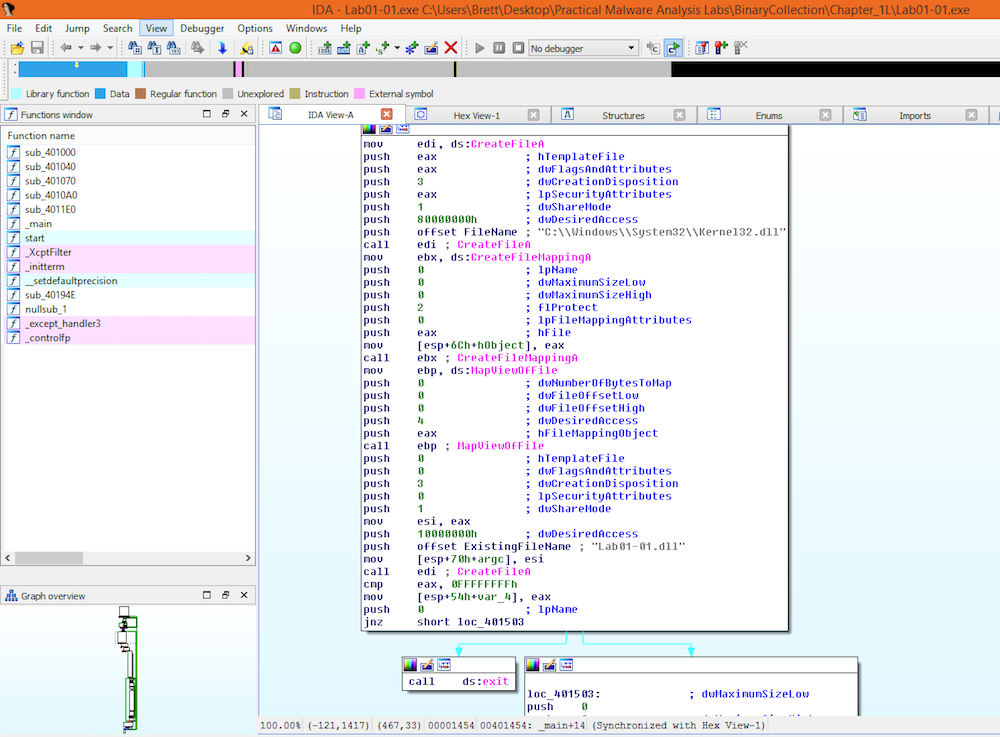
Another technique that can be used to determine if the malware is packed is to utilize IDAPro to see if the instructions seem reasonable and if there is any evidence of jumping to a decoder stub:
Lab01-01.exe
Lab01-01.dll
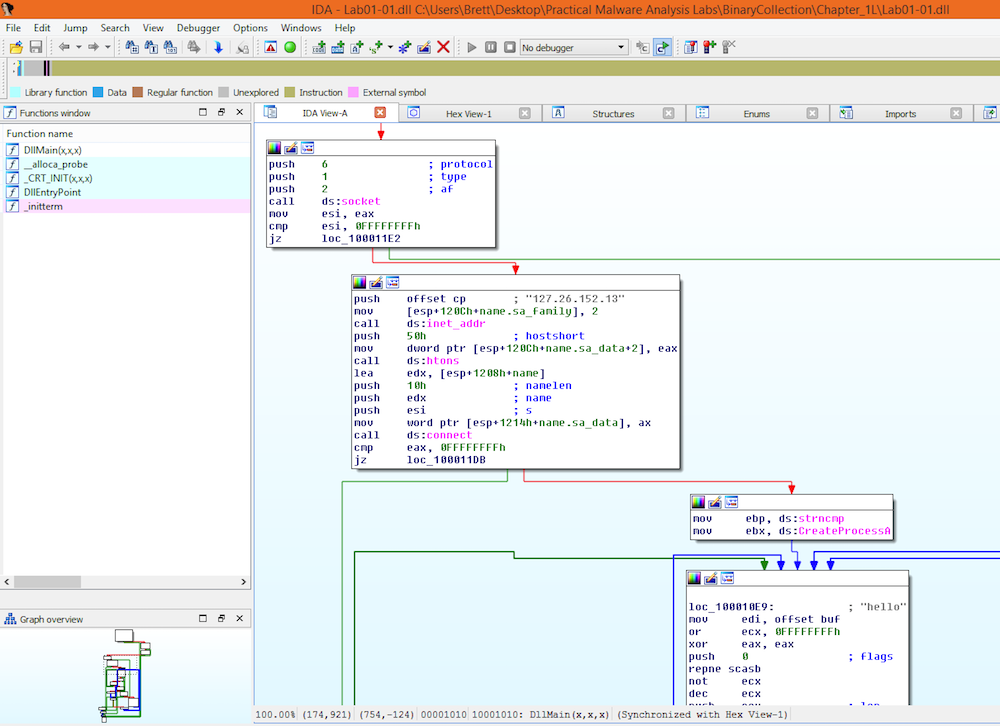
Looking at both the exe and dll within IDAPro show that the instructions do not appear to jump to a decoder stub of any kind and the instructions are clearly visible.
Imports Indicate Malware Functionality?
Do any imports hint at what this malware does? If so, which imports are they?
Lab01-01.exe
The imports of Lab01-01.exe contain:
- CreateFileA
- FindNextFileA
- FindFirstFileA
- CopyFileA
Based on the imports, the executable appears to:
- Search for a file(s)
- Copies a file(s)
Lab01-01.dll
The imports of Lab01-01.dll contain:
- Sleep
- CreateProcessA
- CreateMutexA
- OpenMutexA
- CloseHandle
- socket
- inet_addr
- connect
- send
- recv
- closesocket
Based on these imports it appears that:
- A socket connection is made to an external server and data is sent and received.
- A process is created
- That a process sleeps at some point
Hypothesis
Based on the strings and imports it seems like this is a backdoor
program that creates a socket connection to 127.26.152.13. Usage /
tampering of kernel32 seems likely to occur as well based upon the
FindFile / FindFirstFile usage, the strings C:\*,
C:\windows\system32\kerne132.dll, and
C:\windows\system32\kernel32.dll.
File or Host-Based Indicators?
Are there any other files or host-based indicators that you could look for on infected systems?
A file based indicator of this malware would be:
C:\windows\system32\kerne132.dll. Finding this file on a system
would likely indicate the presence of the malware.
Network-Based Indicators?
What network-based indicators could be used to find this malware on infected machines?
Network activity to 127.26.152.13 would be a network-based indicator
of the malware being present on a system.
Purpose of Files?
What would you guess is the purpose of these files?
Based on the imports and strings in the exe and dll, it would appear that the dll contains backdoor functionality and the exe is used to run, infect, and or install the backdoor.
Conclusion
It was really fun and interesting analyzing and reporting on the first malware in this lab exercise. I look forward to doing again for Lab01-02.exe.

